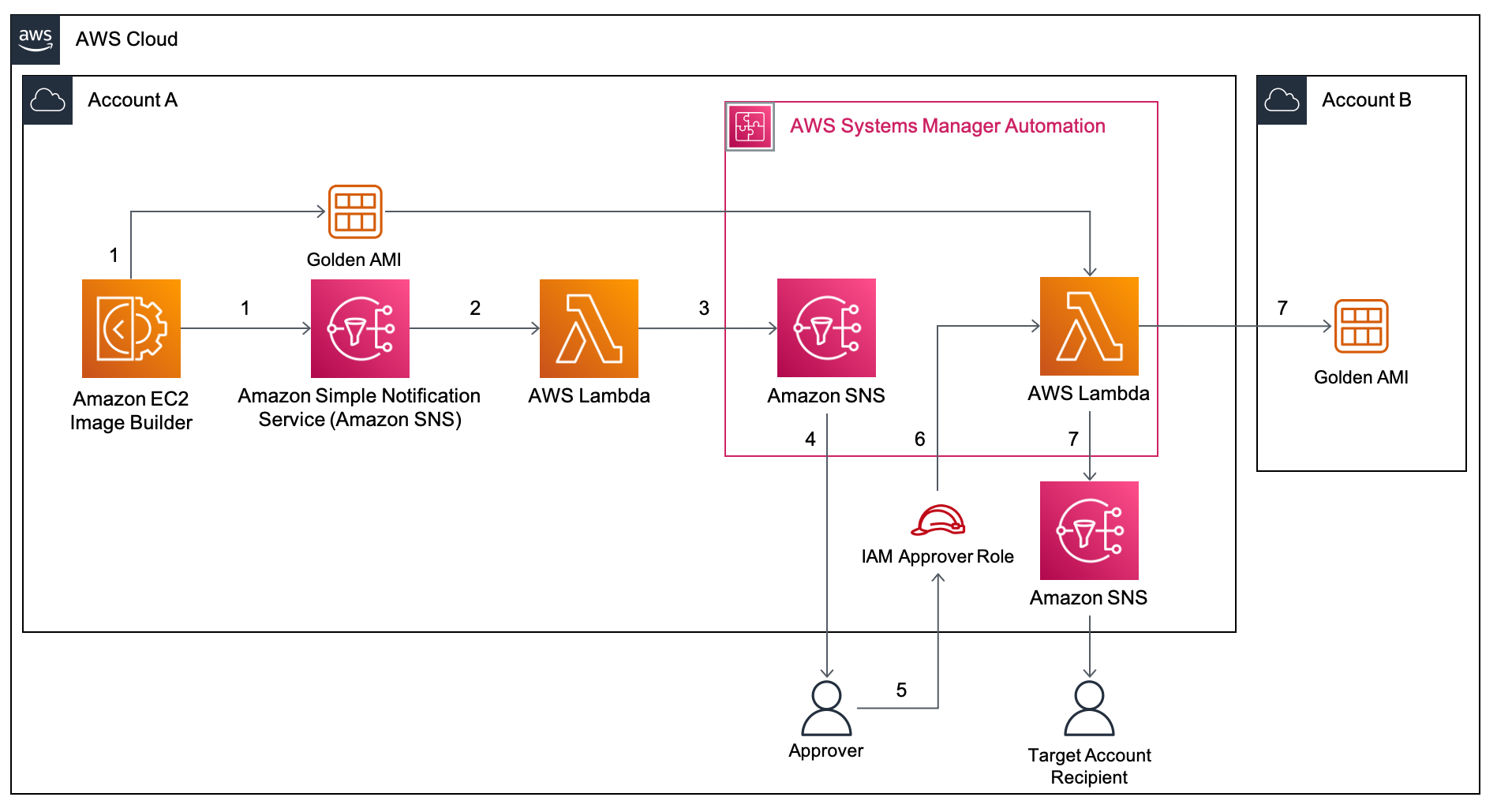
Cloudwatch Events rule triggers Lamda to Quarantine EC2 instance
AWS Certified Security Study Guide: Specialty (SCS-C01) Exam (p. 309). Wiley. Kindle Edition.
As you can see in Figure 8.4, GuardDuty produces a finding that an instance is communicating with an IP address that is an entry node for the TOR Anonymization network. With a simple Amazon CloudWatch Events rule that looks for the UnauthorizedAccess:EC2/TorClient event and triggers an AWS Lambda function that isolates the compromised instance, we can automatically contain the threat. As you can see in Example 8.2, the Python code sets the variable “security_group_id” to a value received as a parameter from the AWS Lambda Function, an environment variable called QUARANTINE_SG, which contains the identifier of the security group that closes all outgoing access to the instance and allows incoming traffic only from the Incident Forensics IP address. Therefore, the code is changing the security groups for that Amazon EC2 instance.
Code is here: https://gitlab.petermatra.design/gitlab-instance-5e679b60/aws-guardduty-lamda-auto-isolate-mailicious-instance